The Metasploit Project is an open-source, computer security project which provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its most well-known sub-project is the Metasploit Framework, a tool for developing and executing exploit code against a remote target machine.
Metasploit helps security and IT professionals identify security issues, verify vulnerability mitigations, and manage expert-driven security assessments.
Minimum System Requirements:
- 2 GHz+ processor
- 2 GB RAM available (4 GB recommended, increase accordingly with VM targets on the same device)
- 500MB+ available disk space
- 10/100 Mbps network interface card
Supported Operating Systems:
- Windows XP, 2003, Vista, 2008 Server, and Windows 7
- Red Hat Enterprise Linux 5.x, 6.x – x86 and x86_64
- Ubuntu Linux 8.04, 10.04 – x86 and x86_64
Required Browser Versions
- Mozilla Firefox 4.0+
- Microsoft Internet Explorer 9
- Google Chrome 10+
Basics Terms of Metasploit
Vulnerability: Vulnerability is a security hole in a piece of software, hardware or operating system that provides a potential angle to attack the system. Vulnerability can be as simple as weak passwords or as complex as buffer overflows or SQL injection vulnerabilities.
Exploit: “Exploit” refers to a well-known bug/hole that hackers can use to gain entry into the system.To take advantage of vulnerability, you often need an exploit, a small and highly specialized computer program whose only reason of being is to take advantage of a specific vulnerability and to provide access to a computer system.
Payload: A payload is the piece of software that lets you control a computer system after it’s been exploited. The payload is typically attached to and delivered by the exploit.
Metasploit Basic Command Tutorial
Msfconsole

Help
Help: it will show you the basic commands of Metasploit.

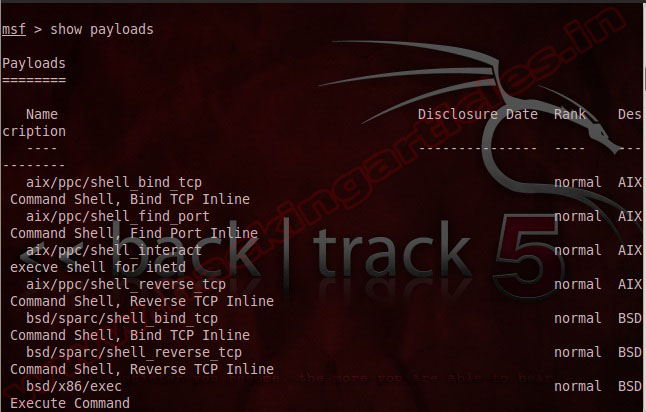
Show payloads
Show payloads: it will show you all the available payloads on Metasploit.
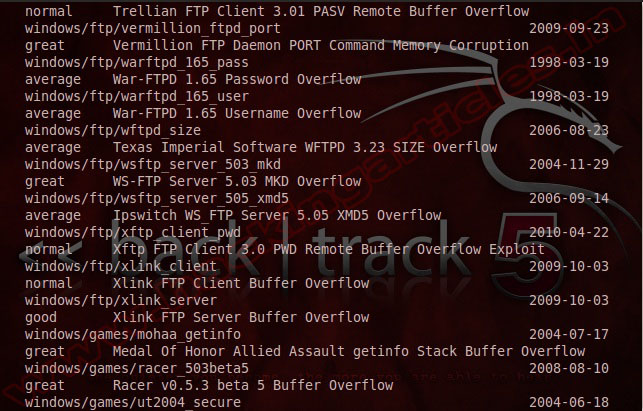
Show exploits
Show exploits: it will show you all exploits in Metasploit.
| msf> use <exploit> | to use a exploit or payload |
| msf exploit (name)> set payload <paload name> | To add specified payload |
| msf exploit (name)> set rhost <victim ip> | To add victim ip address to specified exploit# |
| msf exploit (name)> set lhost <localhost ip> | To add attacker ip address to specified exploit# |
| msf exploit (name)> unset rhost | To remove rhost value |
| msf exploit (name)> unset lhost | To remove lhost value |
| msf exploit (name)> setg rhost <victim ip> | To add victim ip address globally |
| msf exploit (name)> setg lhost <localhost> | To add localhost(attacker) ip address globally |
| msf exploit (name)> sessions -l -v | To see list of sessions |












0 comments:
Post a Comment