USB.Block.1.5.0 || File Size : 3.91 MB.
Key Benefits
Prevent theft of your data: Prevent leakage and copy of your data to USB Drives, External Drives, CDs/DVDs or other such portable devices. Install once and block ALL such drives and devices that do not belong to you. Share your PC without the fear of data theft.
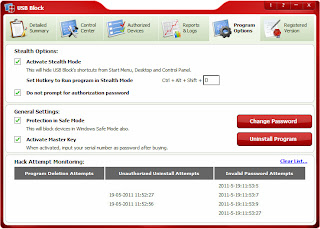
Simple and Effective Device List Management Console: Actively maintain a list of all blocked devices, drives, unauthorized log attempts, uninstall attempts, and invalid password attempts.
Data Leak Prevention at its Best:Use USB Block to protect your data and information against data-leak & data theft. If you leave your computer unattended for long periods of time or if your work environment requires you to actively maintain confidentiality of company data, then you need USB Block!
Strong Monitoring Of All Activities:You can also check Reports & Logs by running the application to regularly monitor which device was authorized, when and by whom. USB Block uses robust data leak prevention technology and ensures complete security of your files at all times.
Protect your PC from Viruses and Spyware: With USB Block, you're in full control of who can access your files and folders. Any malicious attempts by hackers or crackers to install unwanted spying software on your computer can also be prevented with USB Block.
Complete Data Integrity
Block unauthorized USB Drives
Block unauthorized CDs/DVDs
Block unauthorized Network Access
Block unauthorized Drives & Partitions
Save Your Data
Prevent Data Leakage from your PC
Prevent misuse of your data
Prevent viruses & malware attacks
Prevent hackers, crackers and thieves
Hack Monitoring
Monitor program deletion attempts
Monitor fake password attempts
Monitor illegal uninstall attempts
Catch the culprit red-handed